In the rapidly evolving landscape of the Internet of Things (IoT), the ability to securely and reliably manage devices remotely is no longer a luxury but a fundamental necessity. This article delves deep into the powerful synergy of remoteiot vpc ssh raspberry pi, offering a comprehensive guide to establishing a robust, secure, and efficient remote management system for your IoT deployments. Whether you're a hobbyist looking to control a smart home project from afar or a professional deploying a fleet of industrial sensors, understanding how to leverage Virtual Private Clouds (VPCs) and Secure Shell (SSH) with the versatile Raspberry Pi is paramount for success and security.
The challenge of connecting and controlling countless devices scattered across diverse geographical locations presents significant hurdles, particularly concerning security and network isolation. Traditional methods often fall short, exposing devices to potential vulnerabilities or creating complex, unmanageable network configurations. By embracing the principles of VPC for network segmentation, SSH for encrypted communication, and the Raspberry Pi as a low-cost, high-performance edge device, we can overcome these obstacles, ensuring that your IoT ecosystem remains protected, accessible, and fully functional, regardless of its physical distribution.
Table of Contents
- The Foundation of Remote IoT: Understanding the Need
- Why Raspberry Pi? The Heart of Your Edge IoT Device
- Demystifying Virtual Private Clouds (VPCs) for IoT Security
- SSH: Your Secure Gateway to Remote Raspberry Pi Control
- Integrating RemoteIoT VPC SSH Raspberry Pi: A Step-by-Step Approach
- Advanced Security Considerations for Your Remote IoT Ecosystem
- Troubleshooting Common Issues in Remote IoT Deployments
- The Future of Remote IoT: Scalability and Innovation
The Foundation of Remote IoT: Understanding the Need
The proliferation of IoT devices across various sectors, from smart agriculture to industrial automation, has underscored the critical importance of effective remote management. Imagine a network of environmental sensors deployed across a vast agricultural field, or smart city infrastructure monitoring traffic flow and air quality. Physically accessing each device for maintenance, updates, or data retrieval is often impractical, costly, and time-consuming. This is where the concept of remote IoT truly shines, enabling centralized control and monitoring from anywhere in the world. However, this convenience comes with inherent security challenges. Exposing IoT devices directly to the public internet without proper safeguards can lead to severe vulnerabilities, making them targets for cyberattacks, data breaches, or even physical damage. The need for a secure, private, and robust remote access solution is therefore paramount. This solution must ensure data integrity, device availability, and protection against unauthorized access, laying the groundwork for reliable and scalable IoT deployments.
Why Raspberry Pi? The Heart of Your Edge IoT Device
The Raspberry Pi has emerged as an undisputed champion in the world of IoT, and for good reason. Its compact size, low power consumption, affordability, and incredible versatility make it an ideal choice for a wide array of edge computing applications. Unlike more specialized microcontrollers, the Raspberry Pi runs a full-fledged Linux operating system (typically Raspberry Pi OS, formerly Raspbian), which provides a familiar and powerful environment for developers. This allows for easy installation of software, scripting, and integration with various sensors and actuators.
For remote IoT projects, the Raspberry Pi's capabilities are particularly valuable. It supports a wide range of connectivity options, including Wi-Fi, Ethernet, and Bluetooth, making it adaptable to different network environments. Its GPIO (General Purpose Input/Output) pins enable direct interaction with physical components, transforming it into a bridge between the digital and physical worlds. Furthermore, the extensive community support and vast ecosystem of libraries and tools available for the Raspberry Pi significantly accelerate development cycles and simplify troubleshooting. When considering a robust and flexible platform for your remoteiot vpc ssh raspberry pi setup, the Raspberry Pi stands out as an excellent choice, balancing performance with accessibility.
Demystifying Virtual Private Clouds (VPCs) for IoT Security
A Virtual Private Cloud (VPC) is a virtual network dedicated to your cloud account, logically isolated from other virtual networks in the cloud. Think of it as your own private, secure segment of the internet within a larger public cloud infrastructure (like AWS, Azure, or Google Cloud). This isolation is crucial for IoT security, as it allows you to define your own network topology, including IP address ranges, subnets, route tables, and network gateways. Instead of exposing your Raspberry Pi devices directly to the public internet, you can place them within a private subnet of your VPC. This significantly reduces their attack surface, as they are not directly reachable from the outside world unless you explicitly configure pathways.
VPCs provide granular control over network traffic using security groups and Network Access Control Lists (NACLs). Security groups act as virtual firewalls at the instance level, controlling inbound and outbound traffic for specific devices. NACLs, on the other hand, operate at the subnet level, providing an additional layer of security. By leveraging VPCs, you can create a secure perimeter around your IoT devices, ensuring that only authorized traffic can reach them and that sensitive data remains within your private network. This level of isolation and control is fundamental to building a secure remoteiot vpc ssh raspberry pi infrastructure.
VPC Architecture for IoT Deployments
Designing an effective VPC architecture for IoT involves several key components. Typically, you'd establish a main VPC in your chosen cloud provider. Within this VPC, you'd define multiple subnets:
- Public Subnet: This subnet would host resources that need direct internet access, such as a Bastion Host (jump server) or a NAT Gateway, which allows instances in private subnets to initiate outbound connections to the internet (e.g., for software updates) without being directly exposed.
- Private Subnet(s): This is where your Raspberry Pi IoT devices would reside. Instances in private subnets cannot be directly accessed from the internet. All inbound connections must pass through a public-facing resource, like the Bastion Host.
Route tables dictate how network traffic is routed within your VPC and to the internet. Internet Gateways (IGWs) enable communication between your VPC and the internet, while Virtual Private Gateways (VPGs) are used for VPN connections, allowing secure communication between your on-premises network and your VPC. By carefully configuring these elements, you create a segmented, secure, and highly controlled network environment for your IoT devices, forming the backbone of your secure remote access strategy.
SSH: Your Secure Gateway to Remote Raspberry Pi Control
Secure Shell (SSH) is the backbone of secure remote administration for Linux-based systems, including the Raspberry Pi. It provides a cryptographic network protocol that enables secure data communication between two networked devices. Unlike older, unencrypted protocols like Telnet, SSH encrypts all traffic, including passwords, commands, and output, making it virtually impossible for unauthorized parties to intercept and read your communications. This encryption is critical when managing devices that might be deployed in less secure environments or when sensitive data is being transmitted.
SSH works by establishing a secure channel over an unsecured network. It authenticates both the client and the server, ensuring that you are connecting to the intended device and that the device is communicating with an authorized user. For Raspberry Pi devices, SSH allows you to execute commands, transfer files, and even tunnel other network services securely. This capability is indispensable for remote maintenance, debugging, and software updates, forming a crucial component of any robust remoteiot vpc ssh raspberry pi setup.
SSH Key Management Best Practices
While SSH supports password-based authentication, using SSH keys is a far more secure and recommended practice. SSH keys consist of a public-private key pair. The public key is placed on the Raspberry Pi (server), and the private key is kept securely on your local machine (client). When you attempt to connect, the server challenges your client, which then uses its private key to prove its identity without ever sending the private key over the network.
Key management best practices include:
- Generate Strong Keys: Use strong encryption algorithms (e.g., RSA 4096-bit or Ed25519).
- Protect Private Keys: Never share your private key. Store it securely, preferably with a strong passphrase.
- Use a Dedicated Key: Avoid using the same SSH key for multiple purposes or devices.
- Regular Rotation: Periodically rotate your SSH keys, especially for critical systems.
- Disable Password Authentication: Once SSH key authentication is configured and working, disable password-based SSH login on your Raspberry Pi to prevent brute-force attacks. This significantly hardens your device's security posture.
Adhering to these practices ensures that your remote access to the Raspberry Pi is as secure as possible, mitigating risks associated with compromised passwords.
Integrating RemoteIoT VPC SSH Raspberry Pi: A Step-by-Step Approach
Bringing together the power of a Virtual Private Cloud, the security of SSH, and the versatility of the Raspberry Pi requires a methodical approach. The goal is to create a secure tunnel from your management workstation into your private VPC, and then into your Raspberry Pi devices, without exposing them directly to the internet.
- Cloud VPC Setup:
- Create a new VPC in your preferred cloud provider (AWS, Azure, GCP).
- Define public and private subnets.
- Configure an Internet Gateway for the public subnet.
- Set up a NAT Gateway in the public subnet if your private Raspberry Pis need outbound internet access (e.g., for updates).
- Create a Bastion Host (a small Linux VM) in the public subnet. This will be your jump server.
- Configure security groups for the Bastion Host (allowing SSH from your IP) and for the private subnet (allowing SSH only from the Bastion Host's security group).
- Raspberry Pi Preparation:
- Install Raspberry Pi OS on your Pi.
- Enable SSH on the Raspberry Pi.
- Configure the Raspberry Pi to connect to your network (Wi-Fi or Ethernet).
- Assign a static IP address to the Raspberry Pi within your private subnet's IP range.
- Copy your public SSH key to the Raspberry Pi's authorized_keys file (e.g., using `ssh-copy-id` from a temporary direct connection or by manually adding it).
- Disable password authentication for SSH on the Raspberry Pi.
- Connecting Securely:
- From your local machine, SSH into the Bastion Host using its public IP address and your private SSH key.
- From the Bastion Host, SSH into your Raspberry Pi using its private IP address and the same SSH key (ensure the private key is also on the Bastion Host or use SSH agent forwarding).
This multi-hop SSH approach ensures that your Raspberry Pi devices are never directly exposed to the public internet, significantly enhancing their security posture. This complete setup exemplifies a secure remoteiot vpc ssh raspberry pi solution.
Setting Up Your Raspberry Pi for Remote Access
Before integrating your Raspberry Pi into the VPC, ensure it's properly configured for remote access:
- Install Raspberry Pi OS: Download the latest Raspberry Pi OS (Lite version is often sufficient for headless IoT applications) and flash it onto an SD card.
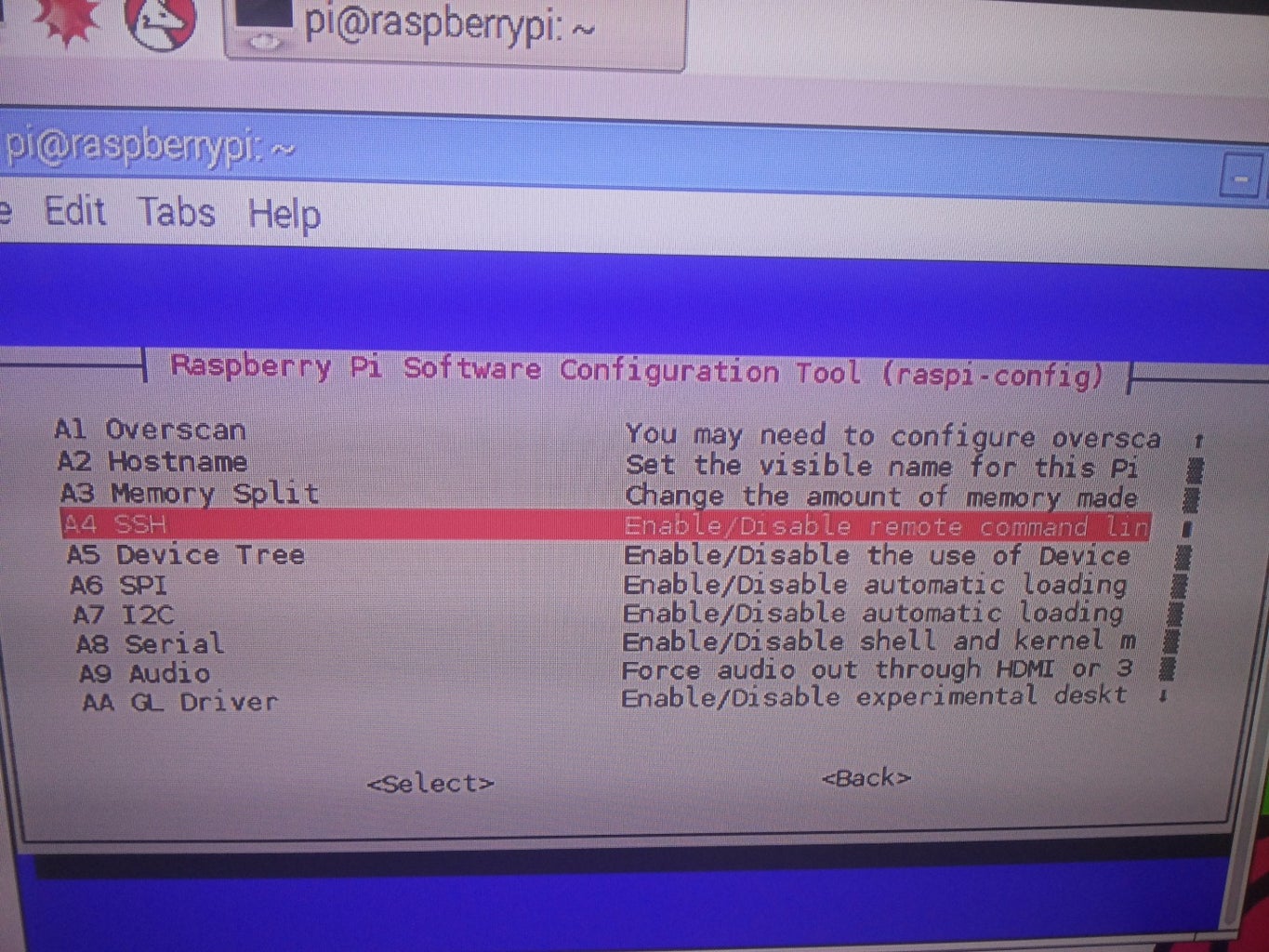
- Enable SSH: Before first boot, you can enable SSH by placing an empty file named `ssh` (no extension) in the boot directory of the SD card. Alternatively, after booting, run `sudo raspi-config`, navigate to "Interface Options," and enable SSH.
- Update and Upgrade: Once logged in, always run `sudo apt update && sudo apt full-upgrade -y` to ensure all software is up-to-date.
- Change Default Password: If you're using password authentication (temporarily, before switching to keys), change the default 'raspberry' password immediately.
- Configure Static IP: For consistent access within your VPC, assign a static IP address to your Raspberry Pi within the private subnet's range. Edit `/etc/dhcpcd.conf` to configure this.
- Copy SSH Public Key: From your local machine, use `ssh-copy-id pi@<Raspberry_Pi_IP>` (if temporarily accessible directly) or manually copy the contents of your public key (`~/.ssh/id_rsa.pub`) to `~/.ssh/authorized_keys` on the Raspberry Pi.
- Disable Password Authentication: Edit `/etc/ssh/sshd_config` on the Raspberry Pi, set `PasswordAuthentication no`, and restart the SSH service (`sudo systemctl restart ssh`). This crucial step significantly enhances security.
These steps prepare your Raspberry Pi to be a secure and manageable endpoint within your remote IoT ecosystem.
Advanced Security Considerations for Your Remote IoT Ecosystem
While the remoteiot vpc ssh raspberry pi setup provides a strong security foundation, continuous vigilance and the implementation of advanced security measures are essential for protecting your IoT ecosystem against evolving threats. Security is not a one-time configuration but an ongoing process.
- Least Privilege Principle: Ensure that your Raspberry Pi devices and the users accessing them only have the minimum necessary permissions to perform their functions. Avoid running services as root unless absolutely necessary.
- Regular Updates: Keep the Raspberry Pi OS and all installed software up-to-date. Software vulnerabilities are frequently discovered and patched, and applying these updates promptly is critical. Automate this process where possible.
- Firewall Configuration: Beyond VPC security groups, configure a local firewall (like UFW on Raspberry Pi) to restrict inbound and outbound connections further. Only allow necessary ports (e.g., SSH from the Bastion Host, IoT platform communication).
- Monitoring and Logging: Implement robust logging on your Raspberry Pi devices and centralize these logs for analysis. Monitor for unusual activity, failed login attempts, or unexpected network traffic patterns. Tools like Splunk, ELK stack, or cloud-native logging services can be invaluable.
- Data Encryption at Rest and In Transit: Ensure sensitive data stored on the Raspberry Pi is encrypted. All communication between the Pi and cloud services should use TLS/SSL encryption, complementing the SSH tunnel.
- Physical Security: For devices deployed in accessible locations, consider physical security measures to prevent tampering or theft of the Raspberry Pi itself.
By layering these security measures, you build a resilient defense against a wide range of cyber threats, safeguarding your IoT devices and the data they handle.
Implementing Bastion Hosts and VPN for Enhanced Security
For even greater security and manageability, especially in larger deployments, consider integrating Bastion Hosts and Virtual Private Networks (VPNs) into your remoteiot vpc ssh raspberry pi architecture.
- Bastion Host: As discussed, a Bastion Host (also known as a jump server) is a hardened server in a public subnet that acts as the sole entry point into your private network segment. All administrative access to your private Raspberry Pi devices goes through this Bastion Host. It should be meticulously secured, with minimal software installed, strong authentication (SSH keys, MFA), and strict firewall rules allowing SSH access only from specific trusted IP addresses (e.g., your office IP). This centralizes access control and provides a clear audit trail.
- VPN (Virtual Private Network): For more complex scenarios or when you need to extend your corporate network securely into the cloud VPC, a VPN is invaluable. You can establish a Site-to-Site VPN connection between your on-premises network and your cloud VPC. This creates an encrypted tunnel, allowing your internal network to directly access resources in the private subnets of your VPC as if they were on the same local network. Alternatively, for individual users, a Client VPN endpoint can be set up, allowing remote employees to securely connect to the VPC from anywhere. VPNs provide an additional layer of encryption and network isolation, making them ideal for sensitive IoT deployments where data confidentiality and integrity are paramount.
Combining Bastion Hosts with VPNs offers a multi-layered security approach, significantly reducing the attack surface and providing secure, auditable access to your remote IoT infrastructure.
Troubleshooting Common Issues in Remote IoT Deployments
Even with the most meticulous planning, issues can arise in remote IoT deployments. Understanding common pitfalls and how to troubleshoot them is crucial for maintaining the reliability of your remoteiot vpc ssh raspberry pi setup.
- SSH Connection Refused:
- Cause: SSH service not running on Pi, firewall blocking port 22, incorrect IP, or SSH disabled.
- Solution: Check `sudo systemctl status ssh` on Pi. Verify security group/NACL rules in VPC. Ensure correct private IP.
- Permission Denied (Public Key):
- Cause: Incorrect permissions on `~/.ssh` or `authorized_keys` on Pi, or incorrect private key on client.
- Solution: On Pi, `chmod 700 ~/.ssh` and `chmod 600 ~/.ssh/authorized_keys`. Ensure your client uses the correct private key (`ssh -i /path/to/your/key`).
- Network Connectivity Issues (Pi):
- Cause: Incorrect static IP configuration, Wi-Fi issues, or no route to the Bastion Host/NAT Gateway.
- Solution: Verify `/etc/dhcpcd.conf` for static IP. Check Wi-Fi connection. Ping the Bastion Host from Pi to confirm connectivity. Ensure NAT Gateway is correctly configured for outbound access.
- Bastion Host Access Issues:
- Cause: Incorrect security group rules on Bastion Host, wrong public IP, or key issues.
- Solution: Double-check security group to allow SSH from your specific public IP. Verify Bastion Host's public IP. Ensure your SSH key is correct for the Bastion Host.
- Device Offline:
- Cause: Power loss, SD card corruption, or software crash on Pi.
- Solution: Implement watchdog timers, power cycle solutions (if safe), and robust SD card management (e.g., read-only file systems for OS). Remote power cycling or KVM-over-IP solutions might be needed for critical deployments.
Thorough logging on both the Raspberry Pi and the cloud infrastructure, combined with proactive monitoring, will significantly aid in quickly identifying and resolving these common issues.
The Future of Remote IoT: Scalability and Innovation
The foundation laid by a secure remoteiot vpc ssh raspberry pi setup is not just about current needs but also about future scalability and innovation. As IoT deployments grow from tens to hundreds or thousands of devices, manual SSH management becomes impractical. This is where automation and orchestration come into play.
- Configuration Management Tools: Tools like Ansible, Puppet, or Chef can automate the provisioning, configuration, and management of multiple Raspberry Pi devices. You can define the desired state of your devices (e.g., installed software, network settings, security configurations) and push these configurations remotely, ensuring consistency and reducing manual effort.
- Centralized Monitoring and Logging: Integrating your Raspberry Pi logs and metrics with cloud-based monitoring solutions (e.g., AWS CloudWatch, Azure Monitor, Google Cloud Logging) provides a unified view of your entire IoT fleet's health and performance. This enables proactive issue detection and performance optimization.
- Containerization (Docker/Podman): Deploying IoT applications in containers on Raspberry Pi devices enhances portability, isolation, and simplifies updates. Containers ensure that applications run consistently across different devices and environments.
- Edge Computing and AI/ML: The Raspberry Pi's growing processing power allows for more sophisticated edge computing, where data processing and analysis occur closer to the source, reducing latency and bandwidth requirements. Integrating AI/ML models on the Pi enables intelligent decision-making at the edge, further enhancing the capabilities of remote IoT systems.
- Zero-Touch Provisioning: For large-scale deployments, explore zero-touch provisioning methods where devices can automatically connect to your VPC and register themselves securely upon first boot, minimizing manual intervention.
The continuous advancements in cloud computing, edge hardware like the Raspberry Pi, and network security protocols ensure that the future of remote IoT is not only secure but also highly scalable, intelligent, and adaptable to an ever-expanding range of applications.
Conclusion
Establishing a secure and efficient remote management system for your Internet of Things devices is paramount in today's interconnected world. By meticulously integrating a Virtual Private Cloud (VPC) for network isolation, Secure Shell (SSH) for encrypted communication, and the versatile Raspberry Pi as your edge device, you can build a robust remoteiot vpc ssh raspberry pi infrastructure that is both secure and highly functional. We've explored the fundamental principles of each component, detailed a step-by-step integration process, and highlighted crucial security best practices, including the use of SSH keys, Bastion Hosts, and VPNs.
The journey into remote IoT is continuous, with evolving technologies and security challenges. However, by adhering to the architectural principles and best practices outlined in this guide, you equip yourself with the knowledge to deploy and manage your IoT devices with confidence, ensuring data integrity, system availability, and protection against unauthorized access. We encourage you to start experimenting with these concepts in your own projects. Share your experiences, challenges, and innovative solutions in the comments below, or explore other related articles on our site to deepen your understanding of secure IoT deployments. Your insights contribute to a stronger, more secure IoT community for everyone.


Detail Author:
- Name : Dr. Guadalupe Willms MD
- Username : nicolas.steve
- Email : federico18@gmail.com
- Birthdate : 1986-08-06
- Address : 1459 Schiller Glens South Donny, WY 46257
- Phone : (870) 836-5338
- Company : Ryan, Hudson and Hamill
- Job : Marking Machine Operator
- Bio : Harum velit error quo aut id veniam. Sit quaerat suscipit nihil. Laborum quibusdam numquam ut aut explicabo facere excepturi.
Socials
facebook:
- url : https://facebook.com/gorczanyh
- username : gorczanyh
- bio : Illo aut qui velit magnam. Nihil et aliquam cumque iure distinctio.
- followers : 5029
- following : 963
linkedin:
- url : https://linkedin.com/in/helena.gorczany
- username : helena.gorczany
- bio : Fugit quia aliquid qui debitis.
- followers : 4949
- following : 651
tiktok:
- url : https://tiktok.com/@helena.gorczany
- username : helena.gorczany
- bio : Consequatur et id sint blanditiis quaerat nobis.
- followers : 6727
- following : 2056
instagram:
- url : https://instagram.com/hgorczany
- username : hgorczany
- bio : Non sint quis ut sunt natus ut. Illo vel assumenda et rerum eum. Quo omnis quasi molestiae impedit.
- followers : 1733
- following : 2255
twitter:
- url : https://twitter.com/helena_gorczany
- username : helena_gorczany
- bio : Debitis eveniet vel dolores amet ut. Laboriosam eos quo consequatur et. Reiciendis eum et dolorum ut laborum nisi in adipisci.
- followers : 5622
- following : 2905